2049-10-18
Back to basics
 I have been doing some theory work, to try to get myself more towards a real-world cyber point of view, instead of my hyper fixations,
I have been doing some theory work, to try to get myself more towards a real-world cyber point of view, instead of my hyper fixations,
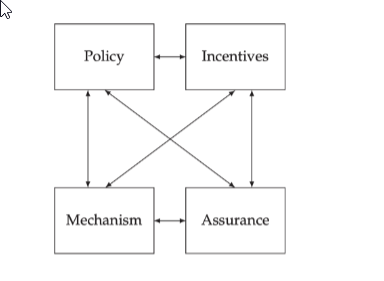
Going through the below framework
I have it interesting to through it in the viewpoint of the target hack of 2013
Policy - Target didn’t have policies in place to ensure that their third-party suppliers had a proper security posture. Specifically, Target granted network access to a third-party HVAC contractor, Fazio Mechanical Services, without verifying their security practices. This lapse allowed attackers to exploit the contractor’s credentials to gain entry into Target’s network. Since then, many organizations now have strengthened their third-party risk management policies. They now require vendors to comply with stringent security standards, conduct regular security audits, and implement continuous monitoring of third-party access. Organizations often use third-party risk management platforms to assess, monitor, and manage vendor risks effectively.
Mechanisms - While the technical mechanism worked, i.e., the FireEye malware detection tool detected the threats, Target didn’t have proper incident response mechanisms to react, allowing the attackers to continue for weeks. Equally worked are the credit card fraud detection systems that start flagging fraudulent transactions.
Assurance - We have information that the FireEye tool was reliable in detecting the malware. Whether the other security mechanisms, such as Intrusion Detection Systems (IDS) and Intrusion Prevention Systems (IPS), worked as expected, we don’t know. Mainly because of the inaction regarding the incident from Target’s side. The “Pass-the-hash” method the attackers used highlighted the limitations of the Single Sign-On (SSO) mechanism without other supplementary mechanisms such as the principle of least privilege.
Incentives - Target, a larger company with a large customer base, was a lucrative target to the attackers. Not to mention, it was also the high-volume holiday shopping season. It is unclear whether Target’s security team had the incentive to do their job properly as they failed to take timely action to the FireEye alarms. It also appears that Target’s management had prioritised holiday season operations rather than timely notifying the impacted customers.
 I have been doing some theory work, to try to get myself more towards a real-world cyber point of view, instead of my hyper fixations,
I have been doing some theory work, to try to get myself more towards a real-world cyber point of view, instead of my hyper fixations,
Going through the below framework
I have it interesting to through it in the viewpoint of the target hack of 2013
Policy - Target didn’t have policies in place to ensure that their third-party suppliers had a proper security posture. Specifically, Target granted network access to a third-party HVAC contractor, Fazio Mechanical Services, without verifying their security practices. This lapse allowed attackers to exploit the contractor’s credentials to gain entry into Target’s network. Since then, many organizations now have strengthened their third-party risk management policies. They now require vendors to comply with stringent security standards, conduct regular security audits, and implement continuous monitoring of third-party access. Organizations often use third-party risk management platforms to assess, monitor, and manage vendor risks effectively.
Mechanisms - While the technical mechanism worked, i.e., the FireEye malware detection tool detected the threats, Target didn’t have proper incident response mechanisms to react, allowing the attackers to continue for weeks. Equally worked are the credit card fraud detection systems that start flagging fraudulent transactions.
Assurance - We have information that the FireEye tool was reliable in detecting the malware. Whether the other security mechanisms, such as Intrusion Detection Systems (IDS) and Intrusion Prevention Systems (IPS), worked as expected, we don’t know. Mainly because of the inaction regarding the incident from Target’s side. The “Pass-the-hash” method the attackers used highlighted the limitations of the Single Sign-On (SSO) mechanism without other supplementary mechanisms such as the principle of least privilege.
Incentives - Target, a larger company with a large customer base, was a lucrative target to the attackers. Not to mention, it was also the high-volume holiday shopping season. It is unclear whether Target’s security team had the incentive to do their job properly as they failed to take timely action to the FireEye alarms. It also appears that Target’s management had prioritised holiday season operations rather than timely notifying the impacted customers.

